Virtual Memory Layout: Mapping Kernel and User Space (x86-64)
Understanding the Address Space Split
Every pointer in your program is a lie. When your C code dereferences
0x7ffff7a0e000, the CPU doesn’t touch that physical memory address. That number passes through four levels of page tables, gets translated by the MMU, checked against privilege bits, and only then does real hardware get accessed. Most developers know virtual memory exists, but few understand the actual layout or why it matters when their production system crashes at 3 AM.
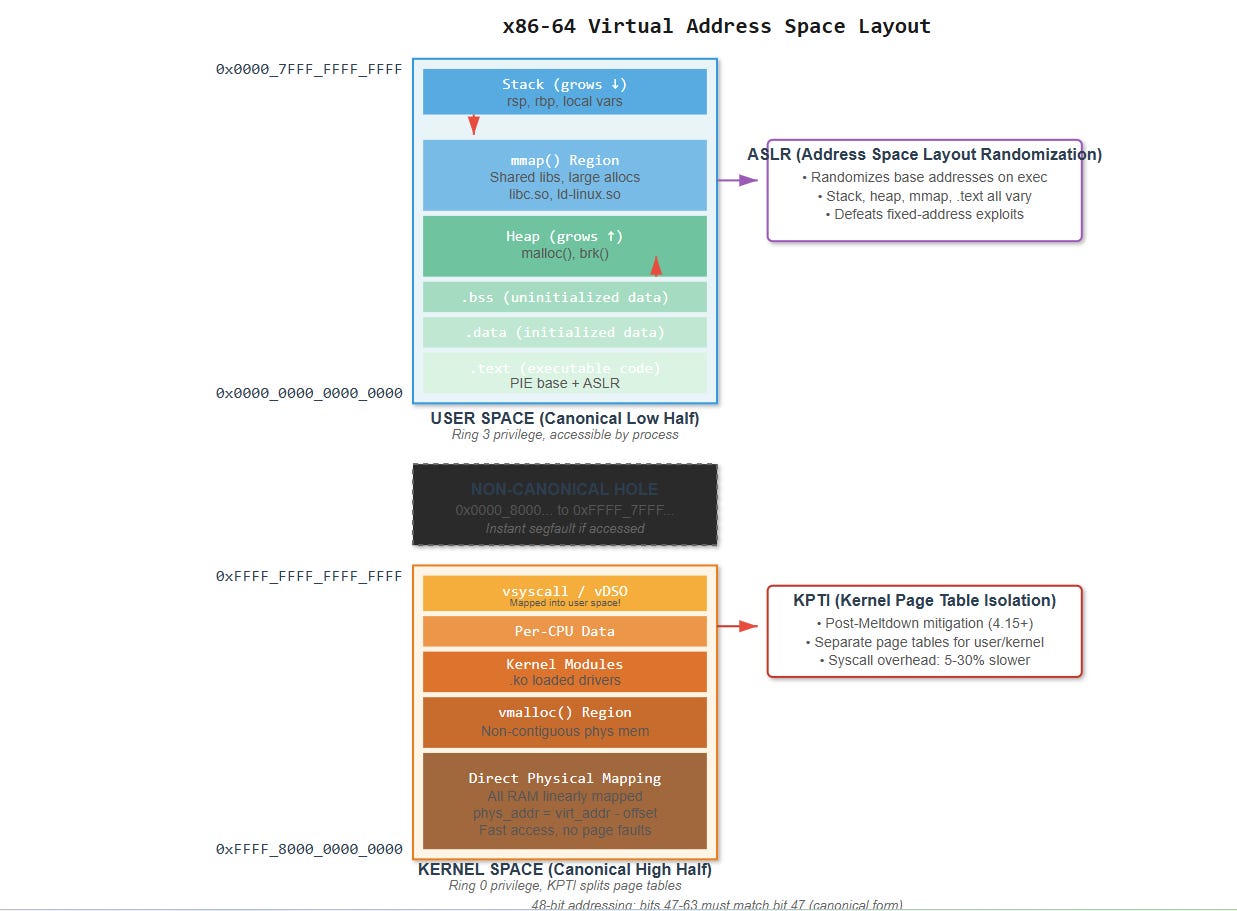
The Address Space Split That Meltdown Exposed
x86-64 gives us “64-bit” pointers, but it’s really 48-bit addressing. The virtual address space has a giant hole in the middle: user space occupies
0x0000_0000_0000_0000through0x0000_7FFF_FFFF_FFFF, kernel space lives at0xFFFF_8000_0000_0000through0xFFFF_FFFF_FFFF_FFFF. Addresses in between are non-canonical and cause instant segfaults. This isn’t academic - try accessing0x0000_8000_0000_0000and watch your process die.